Zero Trust Network Access: Safeguarding the Modern Workplace
As businesses embrace remote work, cloud adoption, and diverse device use, traditional perimeter-based security models are no longer sufficient….
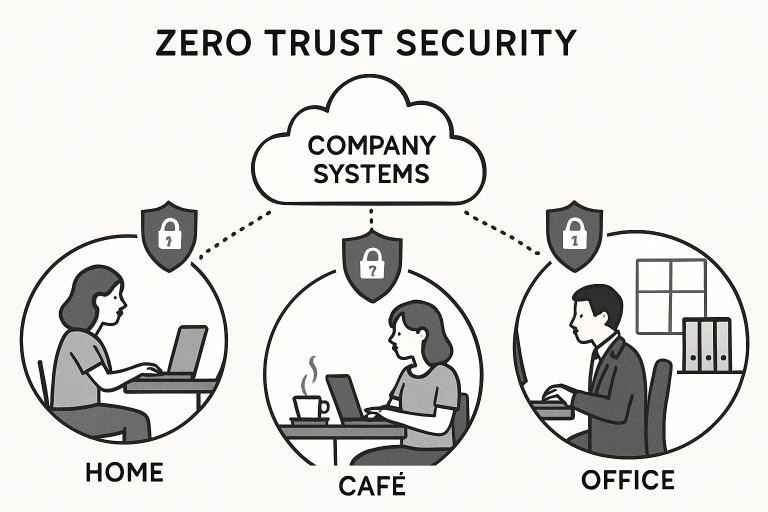
As businesses embrace remote work, cloud adoption, and diverse device use, traditional perimeter-based security models are no longer sufficient….

Introduction In today’s globalized world, television is more than just entertainment, it’s a bridge connecting cultures, languages, and communities…

Introduction In today’s digital-first business landscape, the reliability of cloud-based applications is essential for seamless operations and customer satisfaction….

As Gary Vaynerchuk once said, “Instagram is the ultimate playground for businesses and entrepreneurs.” With over 1.39 billion active…

Overview of Growth Challenges in SaaS Software-as-a-Service (SaaS) companies face unique growth challenges as they scale. Unlike traditional businesses,…

Understanding drive writes per day is essential for evaluating SSD reliability and lifespan. This measure reflects how often data…

Introduction As businesses adapt to rapidly shifting markets, technology, and workforce expectations, the need for modern, flexible approaches to…

The analysis of call patterns associated with mobile number 3301232002 reveals notable trends in frequency and duration. Evening hours…

The mobile call source 96494601 presents a unique case for analysis. Understanding its origins requires a detailed examination of…

The 2033984310 phone number, allocated within Connecticut’s segment of the North American Numbering Plan, warrants careful examination. It serves…
End of content
End of content